Cyber Security Highlights
Think smart, click safe, and stay vigilant

Packet Sniffing and Network Traffic Analysis
Capturing and analyzing network traffic in real time, using tools like Wireshark or writing a basic packet sniffer in Python with the scapy library.

Ransomware Analysis
Ransomware Analysis Involves Examining How Malware Infects, Encrypts Data, And Demands Payment, A Process That Has Evolved To Include Data Theft And AI Capabilities.
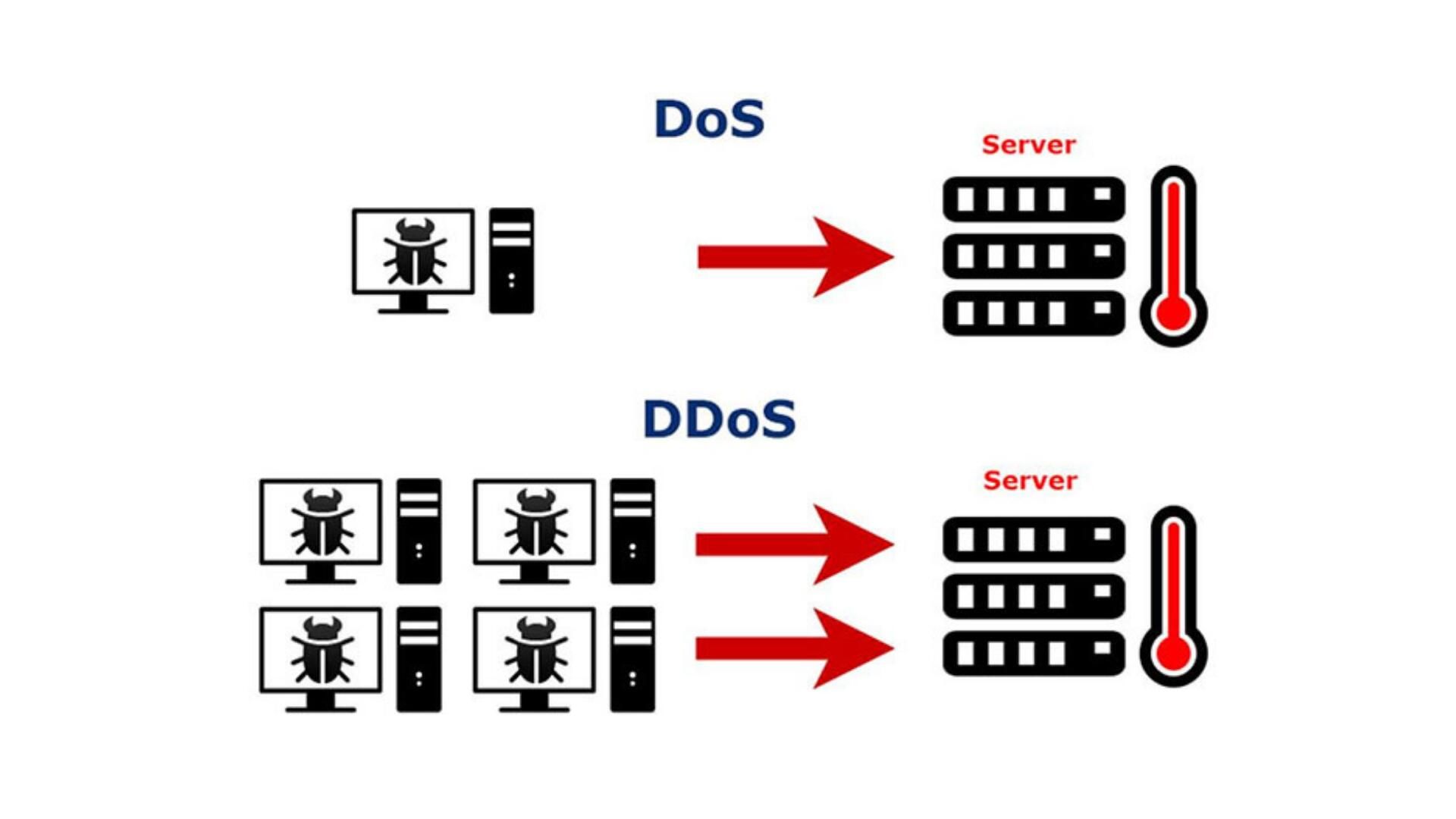
DoS And DDoS Analysis
Collect logs from firewalls, servers, and security services (like Azure WAF).Use a SIEM system, such as Microsoft Sentinel, or a log analytics workspace to query for suspicious activity.

Digital forensics analysis
Digital forensics is a branch of cybersecurity focused on identifying, preserving, analyzing, and documenting digital evidence from devices such as computers, smartphones, and networks related to cybercrime or security incidents.

Threat Intelligence
Threat intelligence is the process of gathering, processing, and analyzing data to understand potential and current cyber threats.The goal is to transform raw data into actionable insights, not just raw data without context.

Malware Analysis
It analyzes the code for patterns, metadata, and indicators like file names, hashes, strings, and imported functions to infer potential behavior, as described on CrowdStrike and Varonis.o quickly identify potential threats or defense evasion techniques.